How To Prevent Data Breaches And What To Be On The Lookout For

Data breaches, an event where a business’s data is stolen, viewed or copied by an unauthorized party, are serious issues in any industry. Today, we’re looking at some of the most likely reasons and ways that data breaches are caused and how to prevent data breaches. Software Vulnerabilities If a piece of software you are […]
Phishing Social Media Quizzes Are Trying To Get Into Your Account

We’re sure you have seen your friends and family sharing quizzes on their social media profiles, asking you to find out what your celebrity name would be or what Hogwarts house you would fall into. While these quizzes are fun and lighthearted, they are also a way to get to know more about people… which […]
6 Types Of Malware You Need To Know About
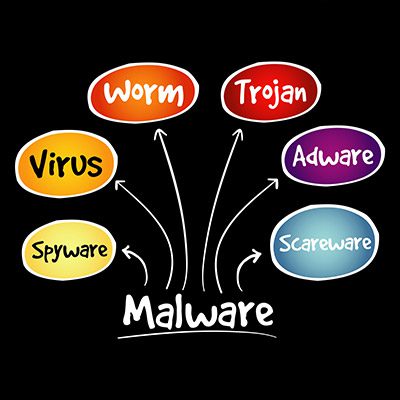
Malware is a blanket term used to describe many different types of security breaks. Today, we’re going to focus on going over the different types of malware so you know the vocabulary and how to identify different types (even though we hope you never have to). What Is malware? The thing about malware is that […]
Tip of the Week: Examining NIST’s Definition of Zero Trust

How many people do you trust? This is a pretty difficult question, but luckily, in a zero trust network, that question is answered for you. The idea of this network is that everyone, no matter who they are, needs to be verified. You might imagine that this has been effective in preventing breaches. But what […]
Have You Heard of Self-Healing Security? MyTek Has The Answers

Have you ever heard of self-healing security? We know this might sound a little out there, but stay with us, we’ll explain. Self-healing security solutions are all about reducing the amount of time it takes to manage security. Self-Healing Security Has Been Developed and Adopted ABN Amro, a major Dutch bank, and Nederlandse Organisatie voor […]
Ransomware is Now Aligned with Terrorism

Ransomware has changed from being an annoyance to being aligned with real global threats. The U.S. Justice Department officially has gone on record and has established that new ransomware investigations will be handled the same way that terrorism is handled. Let’s look into the reasons behind this new strategy and how your own business should […]
Cybersecurity Lessons from the Colonial Pipeline Attack

There has been a ton of news coverage about the recent cybersecurity breach of the Colonial Pipeline, which has caused significant gas shortages on the east coast. While it has not been restored, as the writing of this article, the way it was accomplished sets up a dangerous narrative. This attack has also set off […]
Cyberattack Discovery Time is Decreasing (But This Isn’t All Good News)

Cyberattacks are spending less time on their targeted networks before they are discovered, research revealed. This might sound good on the surface, but unfortunately, it isn’t. Today, we’re going to discuss why cyberattack discovery time is driving more aggressive attack behavior and technology. Dwell Time The amount of time a cyberattack is on the network […]
SolarWinds Hack – Everything You Need to Know

SolarWinds Hack – Everything You Need to Know: True to form, 2020 has given us a final parting gift: the news that the United States was targeted this year by the biggest cyberespionage attack ever. Let’s go into the ramifications of this attack, and what it should teach us going forward. How Did the Attack […]
Employee Monitoring – Are You Crossing The Line? We Can Help

Employee monitoring can seem like such an awkward and divisive topic. As an authority figure on your team, it is pretty important that you are keeping your team on track, and keeping them diligent while they are at work (or while they are working remotely). But, we understand there are some major lines that can […]